Associating a Route 53 Private Hosted zone across AWS accounts
This blog post explains how to associate Amazon Route 53 private hosted zones with VPCs, detailing processes for same-account and cross-account VPC associations, including necessary AWS CLI commands and best practices.

A private hosted zone contains information about how you want Amazon Route 53 to respond to DNS queries for a domain and its subdomains within one or more VPCs you create with the Amazon VPC service.
When you create a private hosted zone, you must associate at least a VPC with the hosted zone, and the VPC(s) that you specify must have been created by using the same account you're using to create the hosted zone. After you create the hosted zone, you can associate additional VPCs with it, including VPCs that you created by using a different AWS account.
You can use the Amazon Route 53 console to associate more VPCs with a private hosted zone if the VPCs and the private hosted zone are hosted in the same AWS account. You can also create these associations programmatically (using the AWS CLI, the AWS SDK, the AWS Tools for Windows PowerShell or calling the Amazon Route 53 API directly).
However, suppose you want to associate a VPC you created in one AWS account with a private hosted zone hosted in a different account. In that case, there is currently no GUI-based option (it's not available in the Amazon Route 53 console), and the only way to achieve this is programmatically (again, using the AWS CLI, the AWS SDK, the AWS Tools for Windows PowerShell or calling the Amazon Route 53 API directly).
In the following sections, I'm going to explain the process to associate a private hosted zone to a VPC in the same AWS account and across AWS accounts.
Steps to associate a private hosted zone and a VPC in the same AWS account
Let's start by seeing how to associate a private hosted zone and a VPC when both are hosted in the same AWS account.
While creating the hosted zone, you can associate it with one or more VPCs (you need to specify at least one).
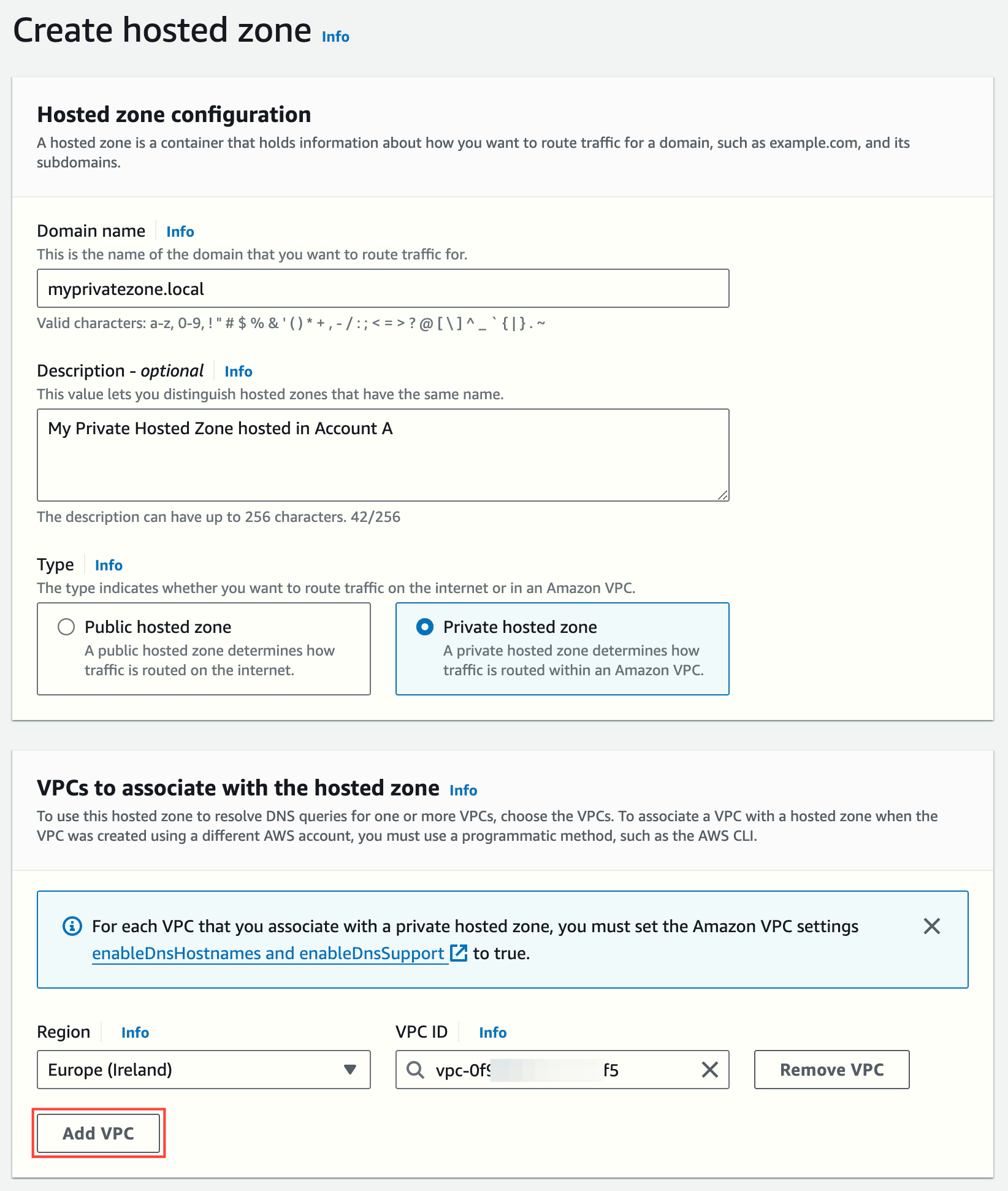
Please notice that for each VPC that you associate with a private hosted zone, you must set the Amazon VPC settings enableDnsHostnames and enableDnsSupport to true.
You can edit the hosted zone later to add, modify or remove VPC associations (in the same AWS account). At least one VPC association must exist.
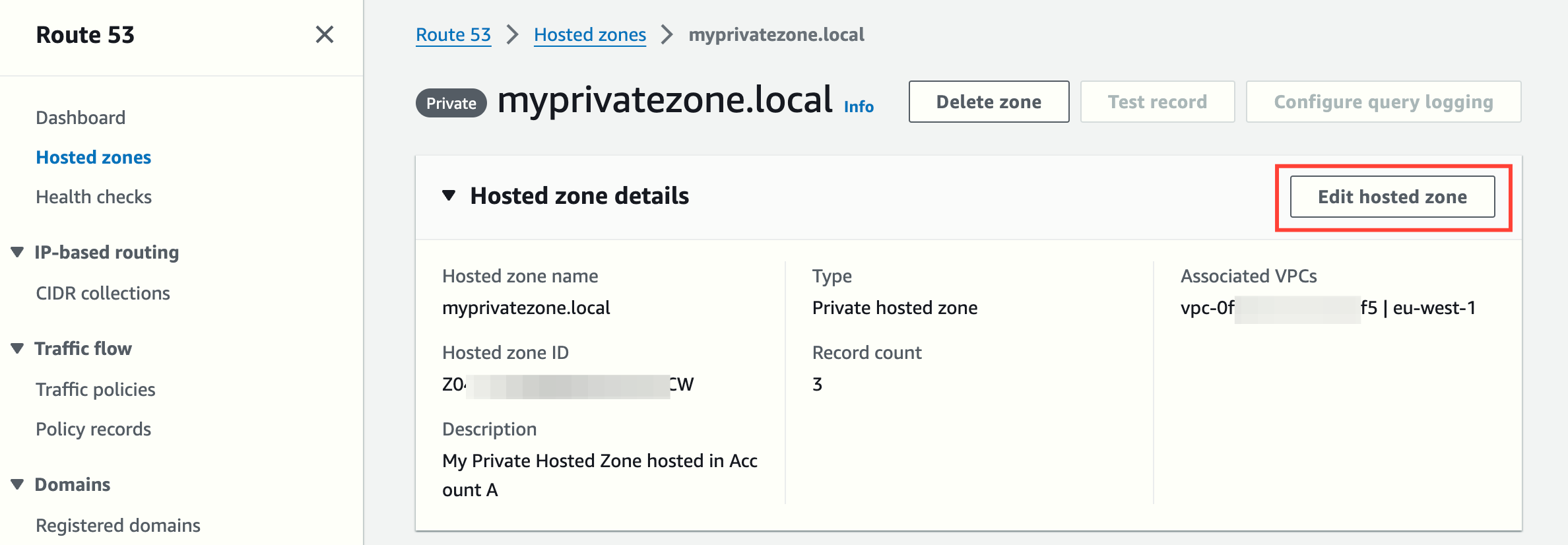
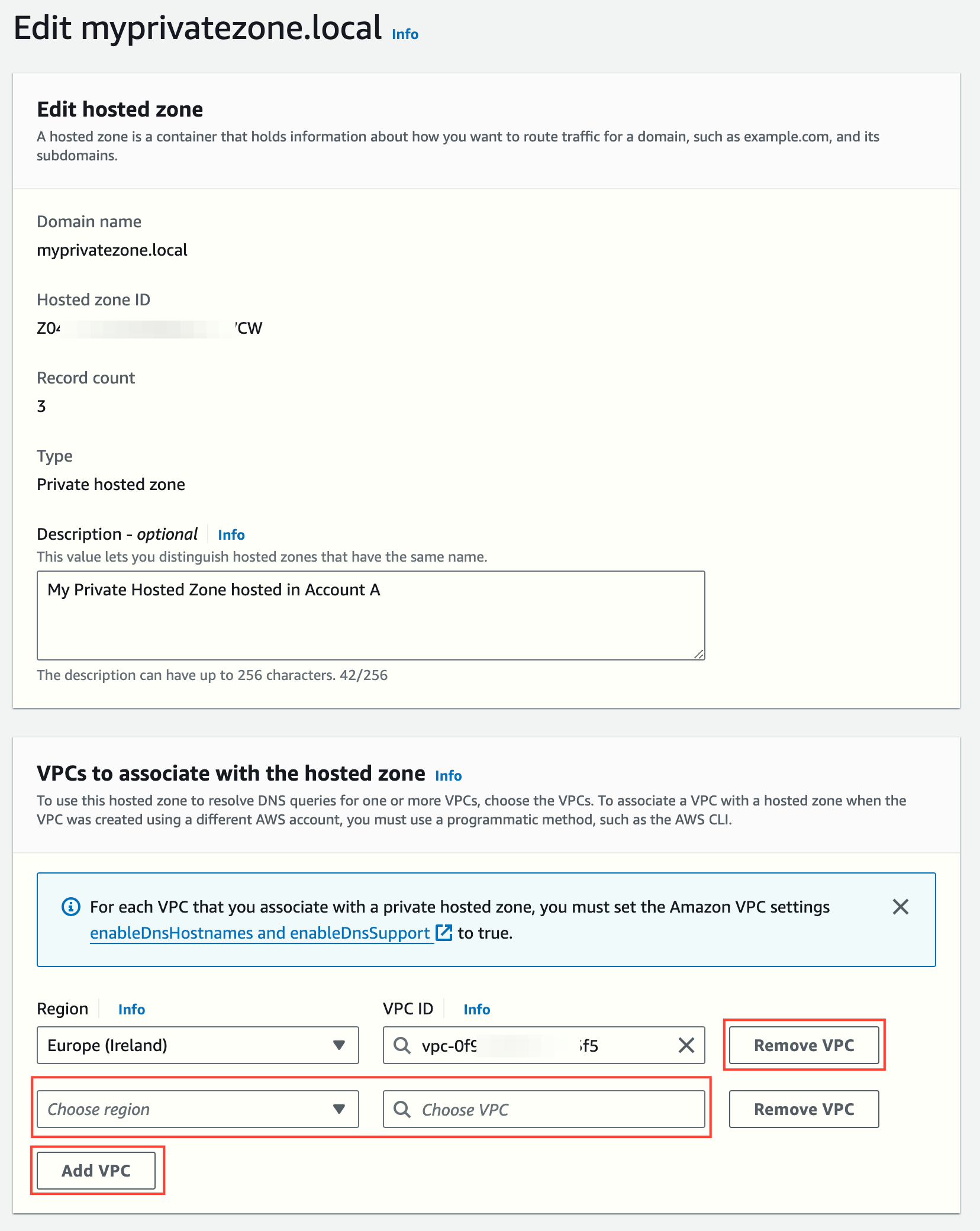
Steps to associate a private hosted zone and a VPC in different AWS accounts
Associating a Route 53 private hosted zone with a VPC in a different AWS account using the AWS CLI involves a few more steps due to the need for cross-account permissions. Let's go through this process with a detailed example.
Example Scenario:
- Hosted Zone Account (Account A):
- AWS Account ID:
123456789012(example ID) - Hosted Zone Domain:
myprivatezone.local - Region:
eu-west-1
- AWS Account ID:
- VPC Account (Account B):
- AWS Account ID:
987654321098(example ID) - VPC ID:
vpc-0987abc6(Assuming this is the VPC ID in Account B) - Region:
us-east-1(assuming the VPC remains in this region)
- AWS Account ID:
NOTE: I will be using AWS CLI Profiles. Ensure that you have the AWS CLI configured with profiles for each account with the necessary permissions in each account to perform these actions. account-a-profile is the AWS CLI profile for Account A and account-b-profile is the AWS CLI profile for Account B.
- In Account A, retrieve the Hosted Zone ID (ZONEID in the following commands, which should look like "/hostedzone/Z04XXXXXXXXXXXXXXXXCW"), either using the Amazon Route 53 console or running the following command:
aws route53 list-hosted-zones --query "HostedZones[?Name=='myprivatezone.local.']" --profile account-a-profile- In Account A, authorize the VPC in Account B to be associated with the hosted zone:
aws route53 create-vpc-association-authorization --hosted-zone-id ZONEID --vpc VPCRegion=us-east-1,VPCId=vpc-0987abc6 --profile account-a-profile- In Account B, associate the VPC with the Hosted Zone:
aws route53 associate-vpc-with-hosted-zone --hosted-zone-id ZONEID --vpc VPCRegion=us-east-1,VPCId=vpc-0987abc6 --profile account-b-profile- In Account A, verify the association:
aws route53 get-hosted-zone --id ZONEID --profile account-a-profile- Test: Configure the necessary DNS records in the hosted zone in Account A and test the DNS resolution from within the VPC in Account B.
- It's a best practice to delete the association authorization after you create the association. This step prevents you from recreating the same association later. In Account A, to list existing VPC association authorizations, delete the authorization and verify the deletion, run the following commands:
aws route53 list-vpc-association-authorizations --hosted-zone-id ZONEID --profile account-a-profile
aws route53 delete-vpc-association-authorization --hosted-zone-id ZONEID --vpc VPCRegion=eu-central-1,VPCId=vpc-1234def5 --profile account-a-profile
aws route53 list-vpc-association-authorizations --hosted-zone-id ZONEID --profile account-a-profile