Enable IAM Identity Center federated users to access an EKS cluster
This article explains how to enable IAM Identity Center federated users to access an EKS cluster's resources.

IAM Identity Center federated users interact with AWS Services by assuming an IAM Role in the AWS Account containing those resources. For this reason, to enable these federated users access to EKS resources, we need to provide permissions to the assumed IAM Role. This article provides the details to achieve this.
If you are new to assigning access to an IAM User and/or IAM Role into an EKS Cluster, please read these two articles:


Identifying the IAM Role assumed by the Federated user
Once we have found the EKS cluster's creator following the instructions above, we must identify the IAM Role that the IAM Identity Center federated users assume.
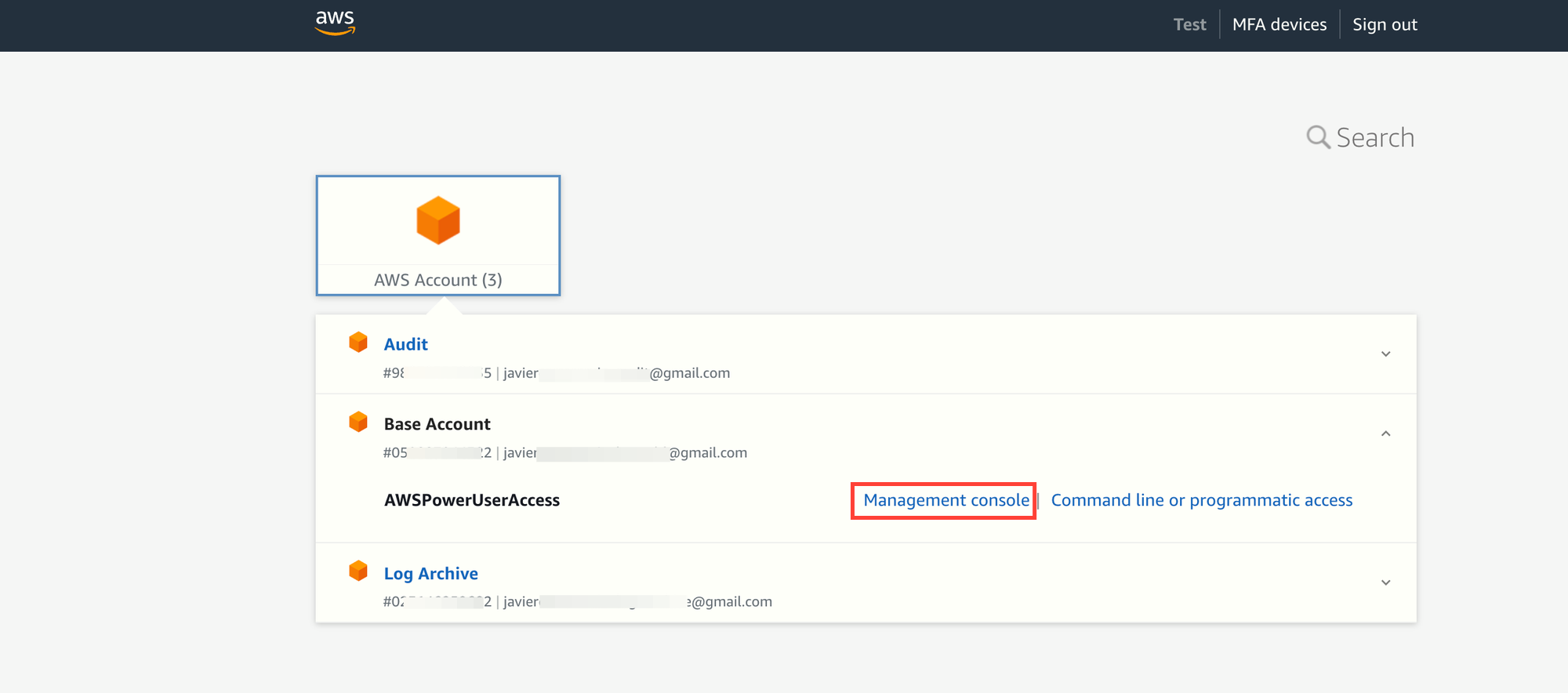
Let's sign in with an IAM Identity Center federated user named testuser@example.com. This use can assume an IAM Role (with AWSPowerUserAccess permissions) in the Base Account.
We choose to open the Management Console with AWSPowerUserAccess permission in the Base Account.
Once we are logged into the AWS Management Console, the connected user's details are shown at the top right of the screen:
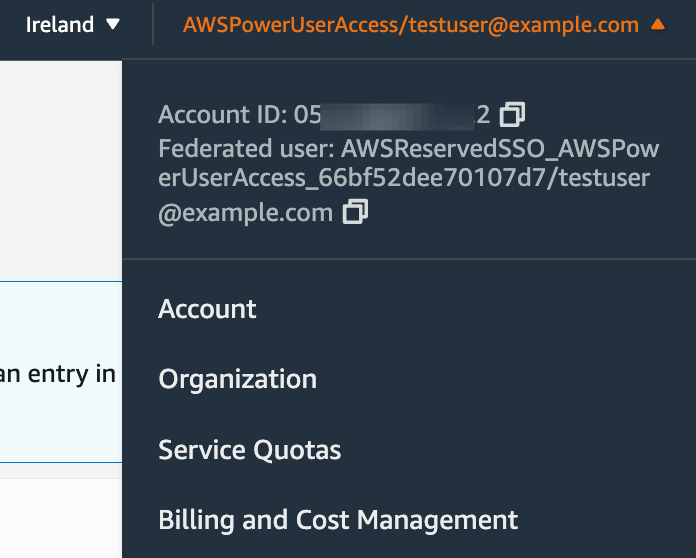
We are interested in the first part of the Federated user string, in this example: AWSReservedSSO_AWSPowerUserAccess_66bf52dee70107d7.
Checking the default visibility of Kubernetes resources by the Federated user
To verify the initially limited visibility of Kubernetes resources, let's look at the resource details on the EKS dashboard for an existing cluster.

Remember: IAM Permissions and Kubernetes RBAC (Role Based Access Control) are initially separated. Our goal is to assign Kubernetes RBAC permissions to an IAM Principal through the aws-auth ConfigMap.Providing access to Kubernetes resources to the Federated user
Once we have the name of the IAM Role assumed by the Federated user, we can add the mapping with a command like this, where <role-name> is the text we extracted from the Federated user string: (AWSReservedSSO_AWSPowerUserAccess_66bf52dee70107d7).
eksctl create iamidentitymapping --cluster <cluster-name> \
--region <region-code> \
--arn "arn:aws:iam::<ACCOUNT-ID>:role/<role-name>" \
--username <kubernetes-user-name> \
--group <kubernetes-group-name> \
--no-duplicate-arns \
--profile <cluster-creator-profile>We can check that the mapping was created by running:
eksctl get iamidentitymapping --cluster <cluster-name> \
--region <region-code> \
--profile <cluster-creator-profile>
If the <kubernetes-group-name> you assign to the mapped identity has permission to list the cluster's pods, you should see something like this:
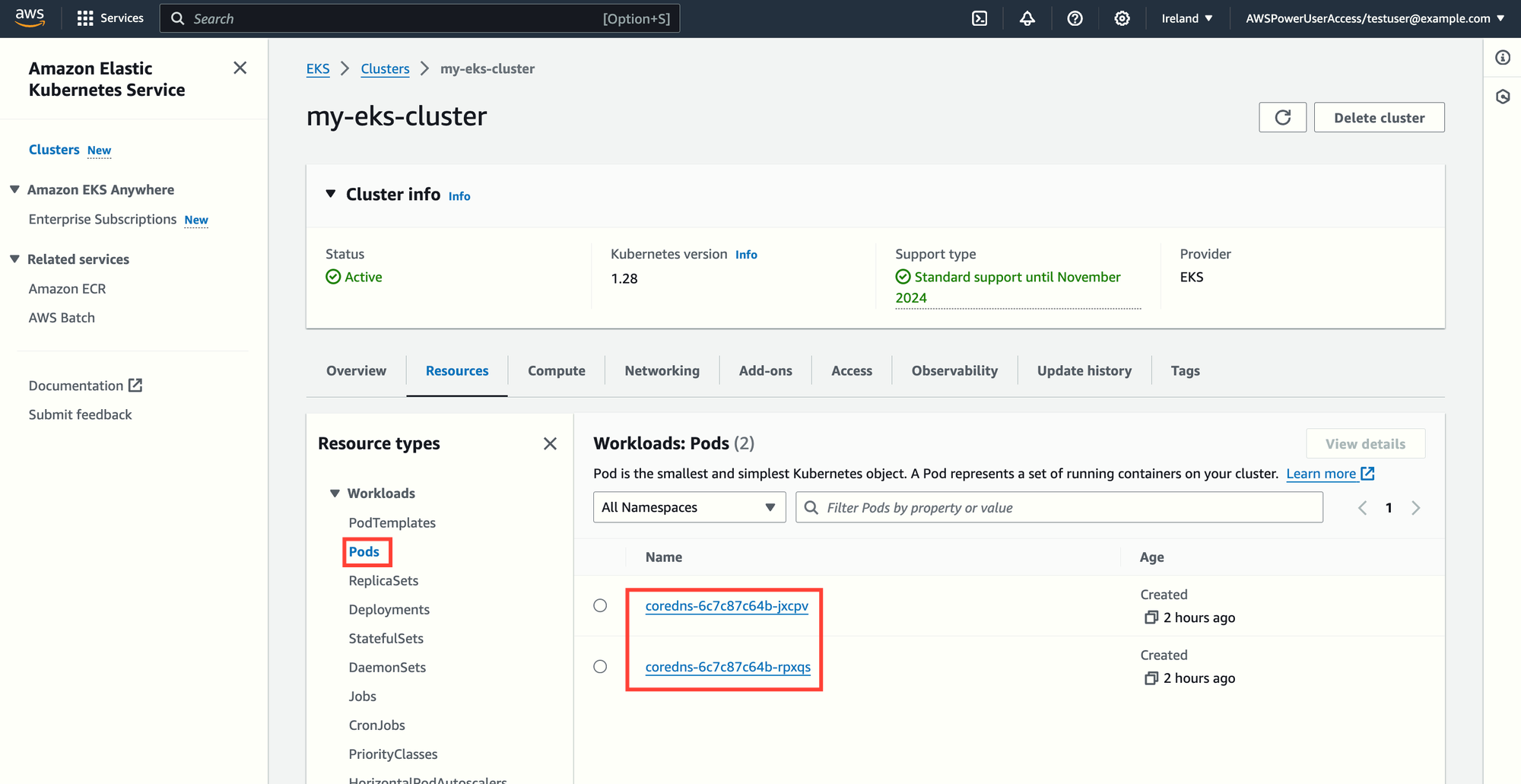
BONUS: Customizing the username field with templates
If you enable the EKS Authenticator logs <kubernetes-user-name>, you can use templates to get dynamic values in the logs instead of setting a static string. The eksctl create iamidentitymapping command would look like:
eksctl create iamidentitymapping --cluster <cluster-name> \
--region <region-code> \
--arn "arn:aws:iam::<ACCOUNT-ID>:role/<role-name>" \
--username {{AccountID}}:identitycenteruser:{{SessionName}} \
--group <kubernetes-group-name> \
--no-duplicate-arns \
--profile <cluster-creator-profile>where :identitycenteruser: is just a random (or empty) string I chose to add. You can set any string or a combination of valid templates or both (as in the example).
Valid templates are: {{EC2PrivateDNSName}}, {{AccountID}}, {{SessionName}}, {{SessionNameRaw}} and {{AccessKeyID}}. See these links for more information: