Run AWS CLI commands with IAM Identity Center federated user credentials
This article explains how to authenticate users with AWS IAM Identity Center credentials to run AWS CLI commands.

If you use IAM Identity Center federated users to manage AWS resources using the AWS Management Console, you might also want to manage them using the AWS CLI (Command Line Interface) using the same identities. This article explains how to authenticate users with AWS IAM Identity Center credentials to run AWS CLI commands.
You can configure the AWS CLI manually (editing the config file directly) or use the aws configure sso wizard (which indirectly edits the config file). In this post, I will only explain the wizard-based option (as it is easier, faster and safer), but I'll show you the final contents of the config file.
Prerequisites
- Install or update the AWS CLI on your machine. The AWS CLI is compatible with Linux, macOS, and Windows, but please check for any specific requirements for those operating systems.
- IAM Identity Center has been configured, and you need at least one federated user.
Configure both an IAM Identity Center profile and sso-session for AWS CLI
We first need to collect some information that the aws configure sso wizard will request. To get it, open the IAM Identity Center portal. Once logged in, find the AWS Account and permission set you want to use:
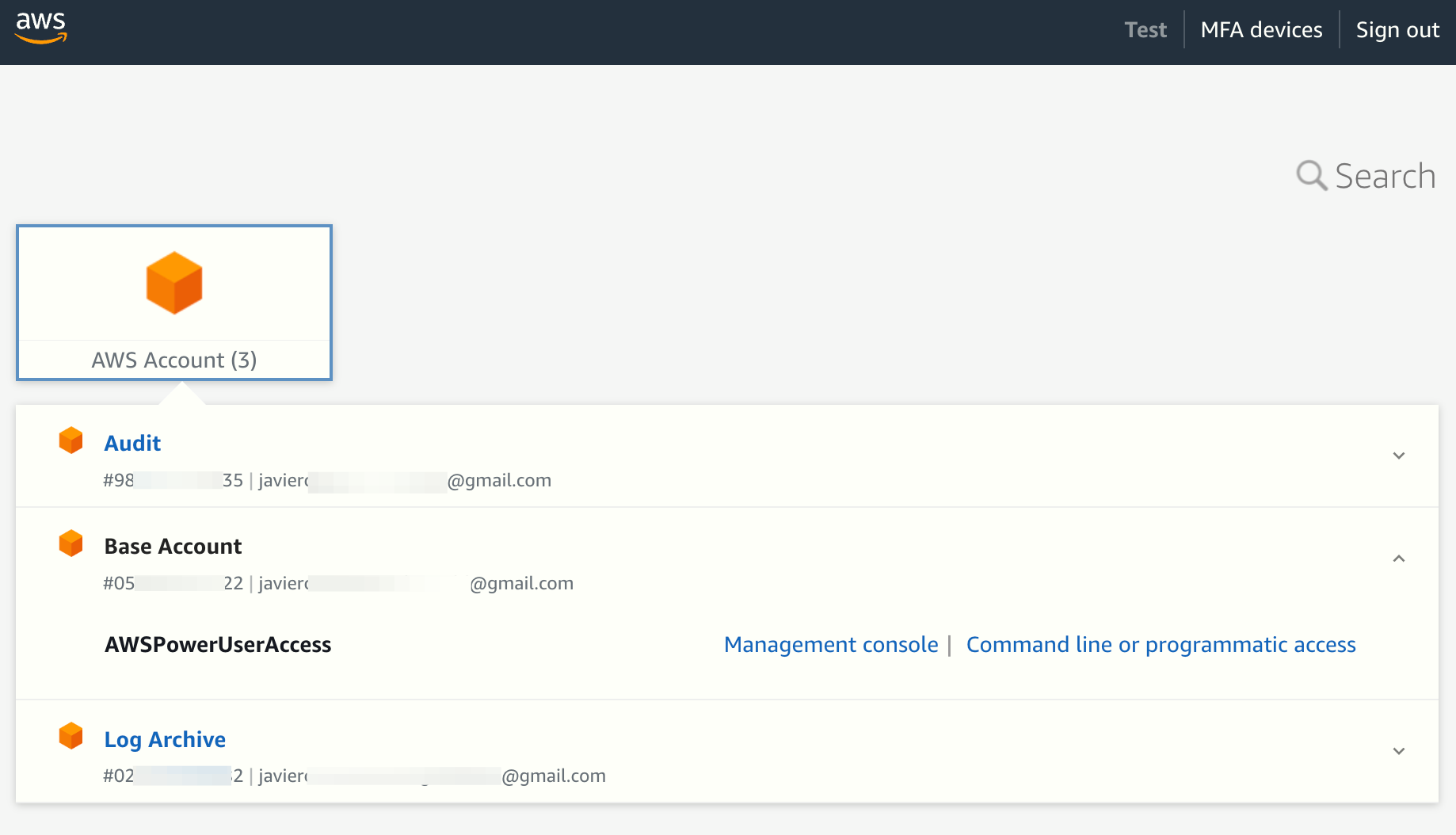
Click on Command line or programmatic access. This will open a pop-up window:
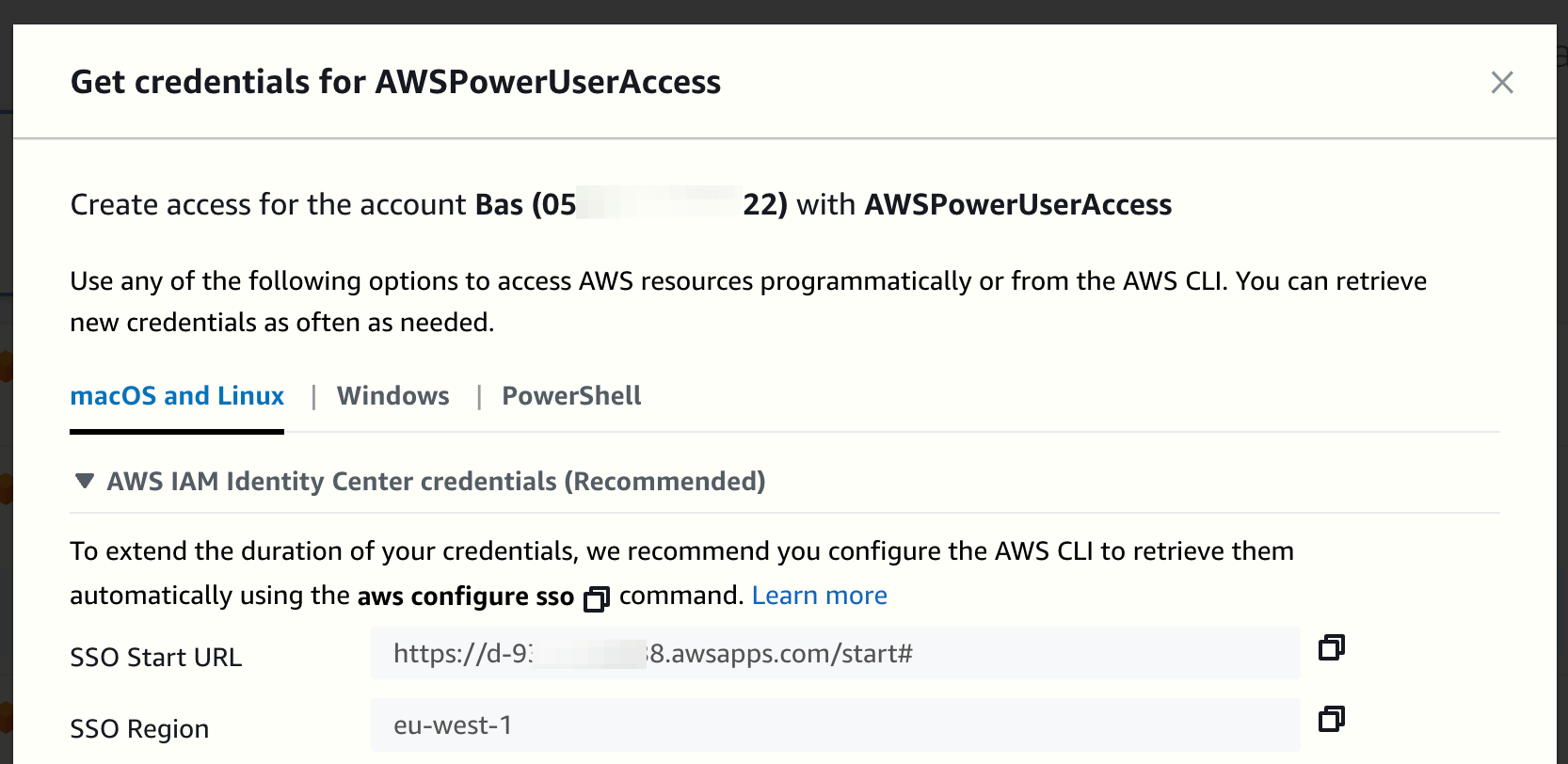
Copy the SSO Start URL and SSO Region values.
We can now configure the AWS CLI with a new profile and sso-session. In your terminal, run the aws configure sso command and enter the requested values. In this case, I'm giving the profile the name my-sso-profile:
aws configure sso --profile my-sso-profileSSO session name (Recommended): my-sso-session-name
SSO start URL [None]: https://d-9XXXXXXXX8.awsapps.com/start#
SSO region [None]: eu-west-1
SSO registration scopes [sso:account:access]:After entering the last value (I typed enter to use the default), the AWS CLI will open your default browser and begin the process in your IAM Identity Center account.
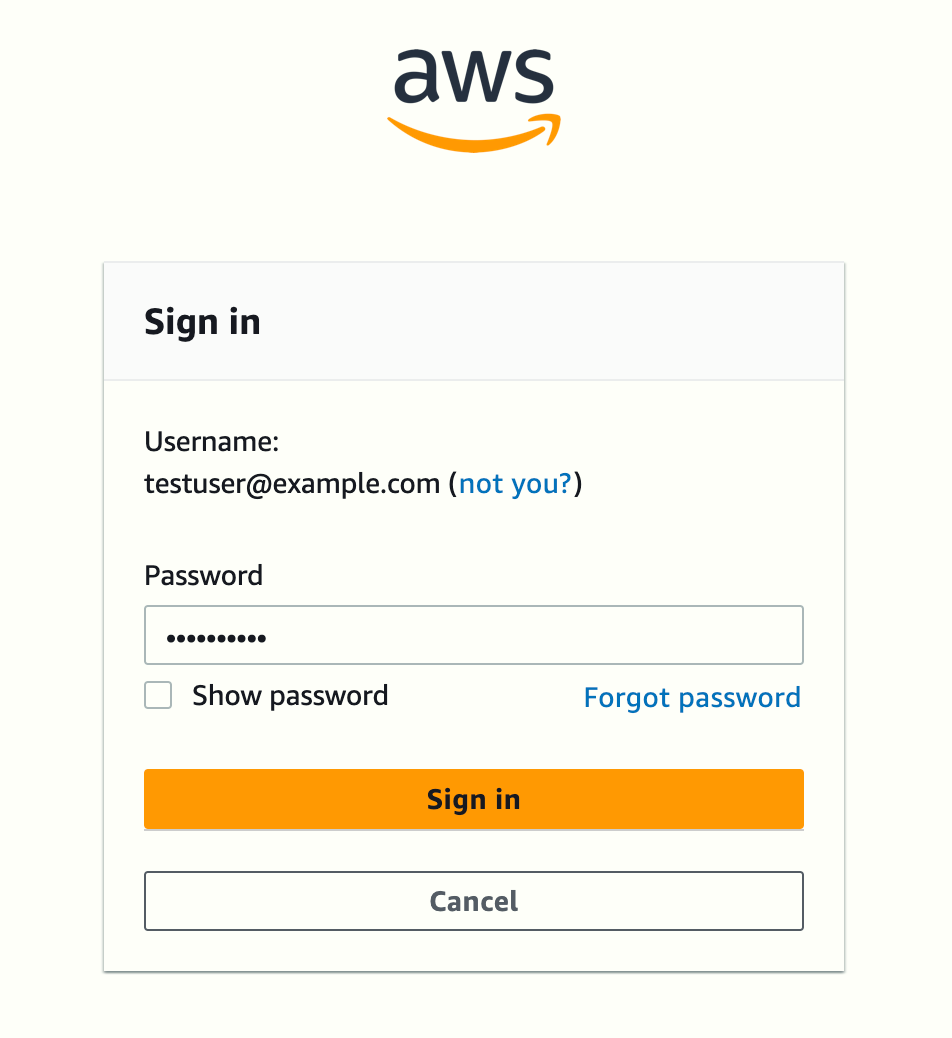
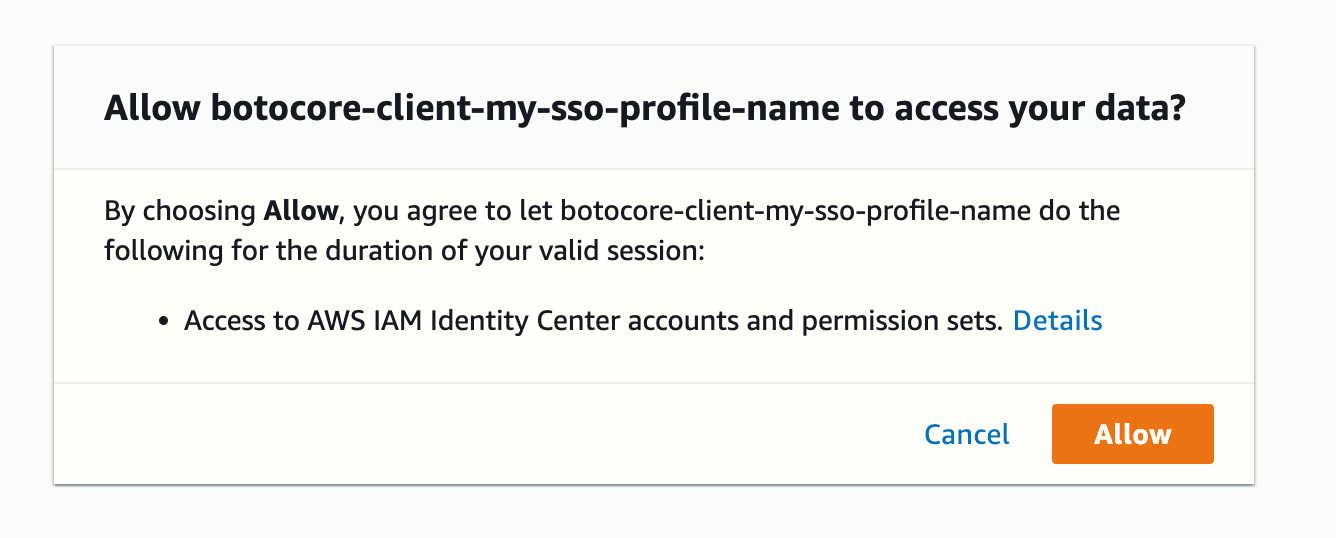
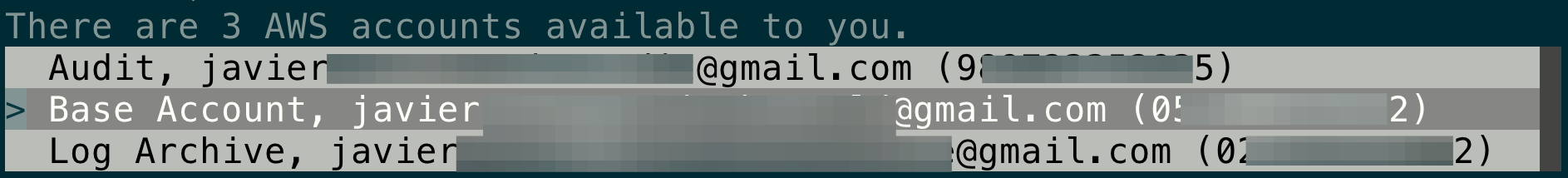
Back in the terminal, as this user can log into multiple accounts, I choose the one I'm interested in.
Then, the wizard prompts for the role I want to assume (if there's only one, it will be selected automatically, otherwise you'll see a prompt similar to the one used to choose the AWS Account).
Finally, you enter the CLI commands' default region and output format.
So, the final output of the aws configure sso --profile my-sso-profile command will look similar to this:
SSO session name (Recommended): my-sso-profile-name
SSO start URL [None]: https://d-9XXXXXXXX8.awsapps.com/start#
SSO region [None]: eu-west-1
SSO registration scopes [sso:account:access]:
Attempting to automatically open the SSO authorization page in your default browser.
If the browser does not open or you wish to use a different device to authorize this request, open the following URL:
https://device.sso.eu-west-1.amazonaws.com/
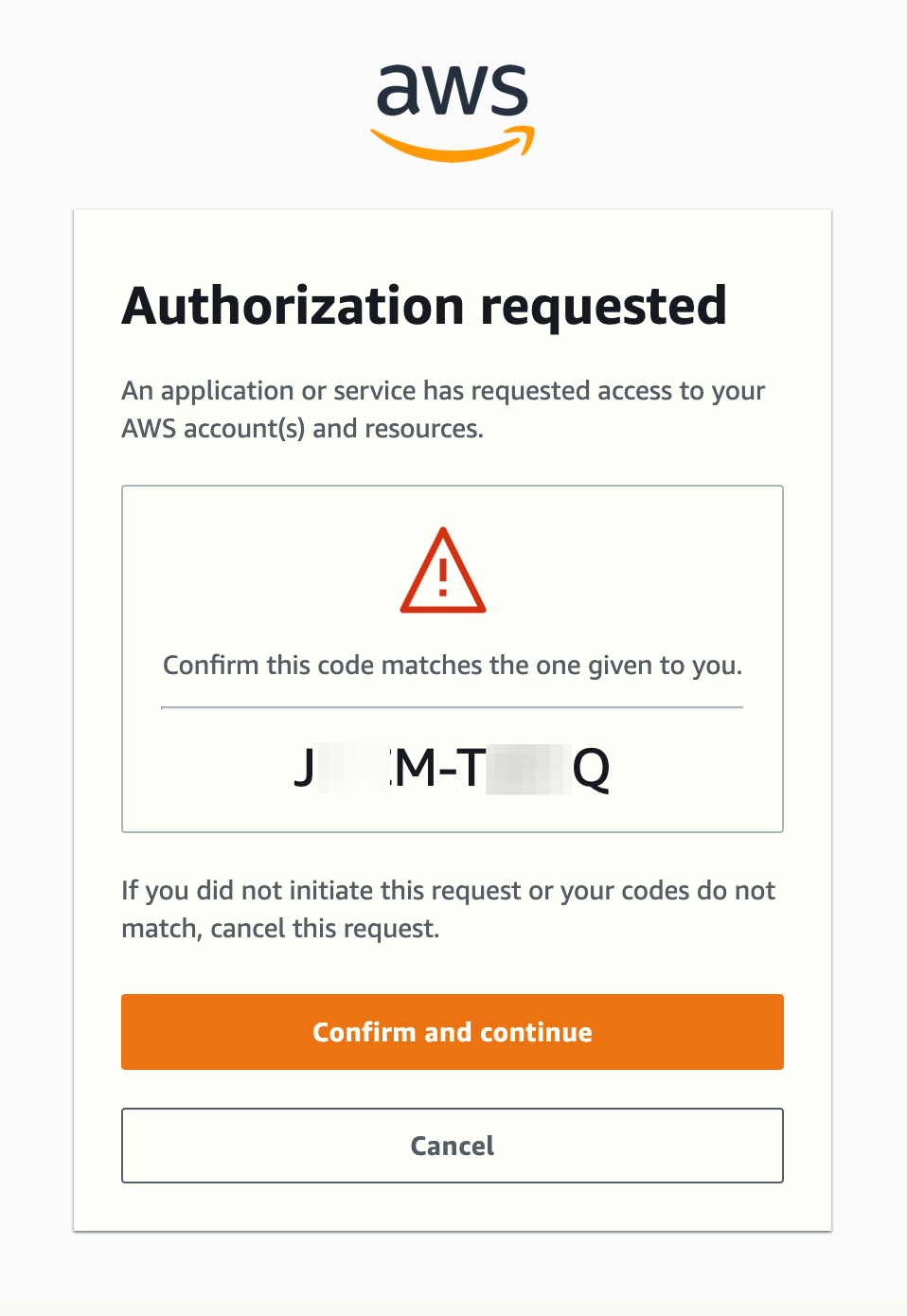
Then enter the code:
JMCM-TVWQ
There are 3 AWS accounts available to you.
Using the account ID 05XXXXXXXX22
The only role available to you is: AWSPowerUserAccess
Using the role name "AWSPowerUserAccess"
CLI default client Region [None]: eu-west-1
CLI default output format [None]: json
To use this profile, specify the profile name using --profile, as shown:
aws s3 ls --profile my-sso-profileIf we inspect the config file, available at ~/.aws/config (on Linux or macOS) or %USERPROFILE%/.aws/config (on Windows), we can see this new content:
[profile my-sso-profile]
sso_session = my-sso-profile-name
sso_account_id = 05XXXXXXXX22
sso_role_name = AWSPowerUserAccess
region = eu-west-1
output = json
[sso-session my-sso-profile-name]
sso_start_url = https://d-9XXXXXXXX8.awsapps.com/start#
sso_region = eu-west-1
sso_registration_scopes = sso:account:accessUsing an IAM Identity Center profile with AWS CLI
Before you can run an AWS CLI command using an IAM Identity Center profile, the tool has to retrieve and cache a set of credentials (unless they are already cached). To do that, run the following command:
aws sso login --profile my-sso-profileThis will open your default browser and trigger the sign in process for your IAM Identity Center account. Once done, we can check our identity:
aws sts get-caller-identity --profile my-sso-profile{
"UserId": "AROAQXWJINCBI321D5Q2Z:testuser@example.com",
"Account": "05XXXXXXXX22",
"Arn": "arn:aws:sts::05XXXXXXXX22:assumed-role/AWSReservedSSO_AWSPowerUserAccess_66bf52dee07107d7/testuser@example.com"
}Note: You can temporarily disable the credentials by logging out withaws sso logout --profile my-sso-profileYou can also sign back in withaws sso login --profile my-sso-profile
From now on, we can use that profile to run any AWS CLI command using the permissions of the IAM Identity Center federated user, e.g.:
aws s3 ls --profile my-sso-profile